Recently, using CloudCoffer SandSphere, we scanned email attachments for our clients and identified various new types of viruses. These viruses share common characteristics: they employ various methods to evade antivirus software, launch targeted attacks on organizations, and attempt to infiltrate internal network systems.
For example, here is the latest virus we detected through our scanning, which no antivirus software has identified on VirusTotal: VirusTotal Link.
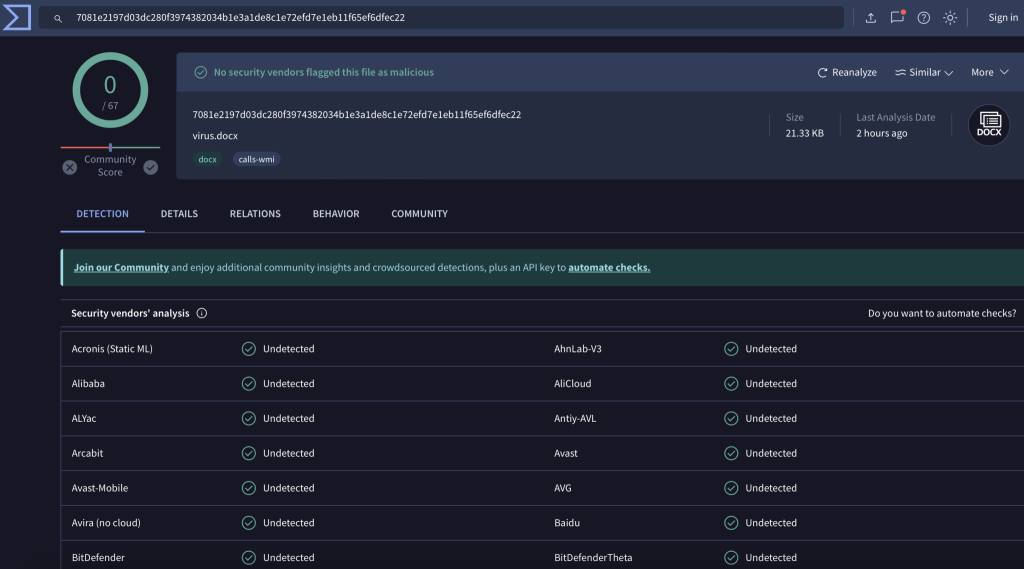
This is a .docx Word file. After analyzing it with SandSphere, CloudCoffer researchers discovered that when the .docx file is opened in Word, it performs a series of malicious activities, such as:
- Executing system commands, one of which is:
IWbemServices::ExecQuery - ROOT\CIMV2 : SELECT * FROM Win32_ComputerSystemProduct - Obtaining sensitive system information (such as website cookies, temporary data, system registry contents, etc.)
- Transmitting sensitive information to 188.114.96.7:443
- Generating additional malicious files
- Using Chrome to send emails and other sensitive information to a remote C&C server (byteburst.cbg.ru)
Therefore, in addition to carefully selecting a defense-in-depth protection system that can perform behavioral analysis, it is crucial to avoid opening any untrusted emails (and regularly conduct social engineering exercises).
