The Intelligent Forbidden Function (TIFF) maximizes both effectiveness and efficiency. Our patent-pending solutions differ from current solutions in many ways.
- We have applied machine learning mechanisms to make rules compact and efficient.
The rules come from many sources as follow.
- Zero-day vulnerability research.
- Honeypots like WASC Distributed Web Honeypot Project.
- Open data like National Vulnerability Database, Exploit-DB, and packetstormsecurity, etc.
- Machine learning deduction.
- There is no reason to apply defense rules for invulnerable systems. TIFF blocks potential risks based on users’ applications, operating systems, and vulnerability. Users may apply rules according to the installed systems or applications.
For example, if a user intends to protect her website built by WordPress, she may simply select WordPress in the menu of TIFF, and TIFF will block malicious requests that affect WordPress. TIFF may also analyze the protected systems and offer rule suggestions.
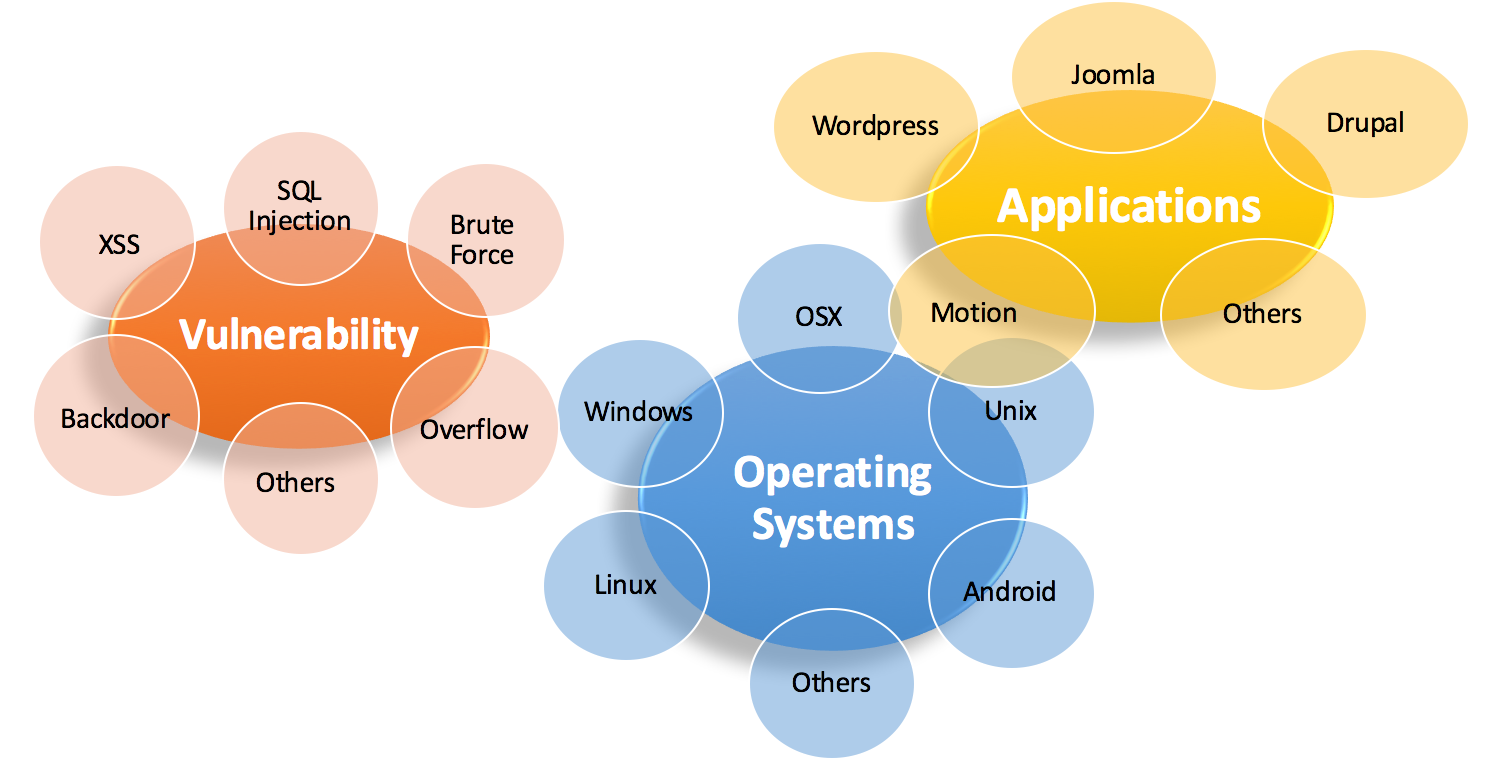
- We provide customized rules for customers, based on the weakness of customers’ systems. CloudCoffer is composed of information security experts, and we have rich experiences identifying vulnerability of systems for banks, governments, enterprises, hospitals, etc. You may submit a request form from here.
